Leveraging Machine Learning in Cyber Asset Inventory
In our recent product announcement, we introduced new capabilities designed to help security teams to better understand and interpret the security data they have. Data accuracy and consistency is a common challenge for Cyber Asset Attack Surface Management (CAASM) platforms, as we ingest data from a wide range of different systems and tools, with different naming conventions and descriptions.
A core feature of Noetic’s CAASM solution is its ability to correlate and unify information about a cyber asset (server, workstation, network device, user, etc.) from multiple data sources, including cloud providers, vulnerability scanners, endpoint security and management systems, CMDB’s, etc. Where correlation provides the “de-duplication” of asset records from multiple data sources, unification provides the best description of an asset from its various sources.
Noetic customers are then able to query this unified, correlated asset data – either by using our simple, spreadsheet-like interactive table (Data Insights), or by building out more complex queries, using the standards-based Cypher query language, that take advantage of our extensible Data Model.
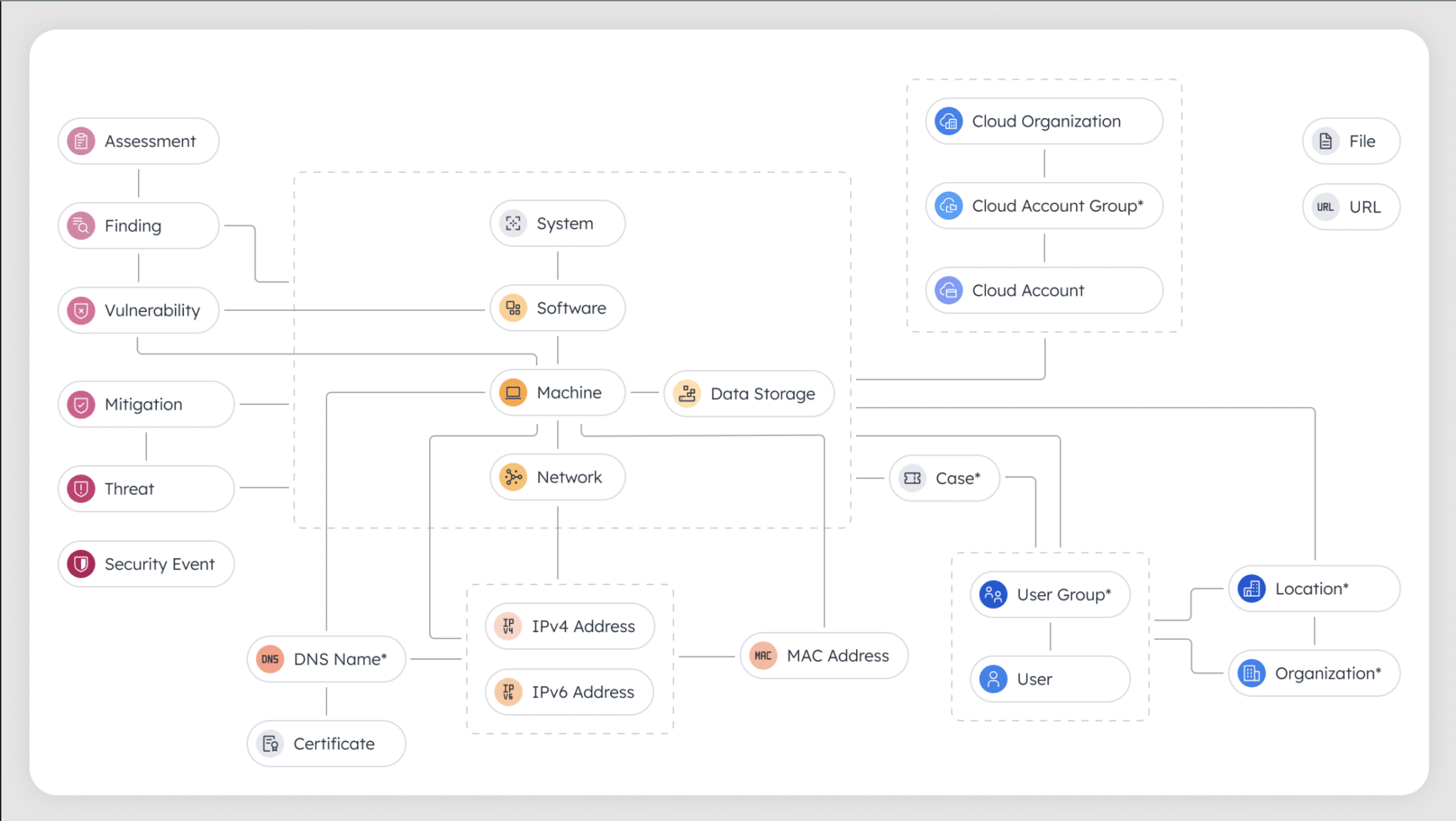
For either approach, the task is much simpler if there is a consistent language used for common asset properties that will typically be used for filtering. Examples of these common properties would include:
- Operating System (OS) family (Windows, Linux, macOS, Cisco, ESXi, etc.)
- Asset Type (Server, Workstation, Network Device, Printer, etc.).
The challenge here is to determine the most accurate value for these unified properties using the information provided by the relevant data sources for each asset. For some assets, we may have information from high-fidelity endpoint agents that can provide accurate, detailed information on type, OS, version number and more. For other assets, we may be reliant on typically less accurate ‘off-board’ data sources, such as external network scanners or a Configuration Management Database (CMDB).
In some cases, a data source may provide useful “make” and “model” information, but not specific OS or asset type information. For example, a CMDB may tell us that an asset is an Apple iPad, and we can therefore infer that the operating system family is “iOS,” and the asset type is “Tablet.” One approach for a CAASM solution such as Noetic would be to build a big rules engine that would be both complex and tough to maintain over time. Fortunately, there are other, more scalable approaches.
To solve this problem and make it easy for security analysts to build queries across large datasets, Noetic leverages machine learning (ML). Specifically, we use predictive large language models (LLM’s), to solve this problem by training natural language classification models with large samples of real-world combinations of source data to develop classifiers which provide “OS Family” and “Asset Class” properties that are consistent no matter what combination of asset data sources are provided by a customer.
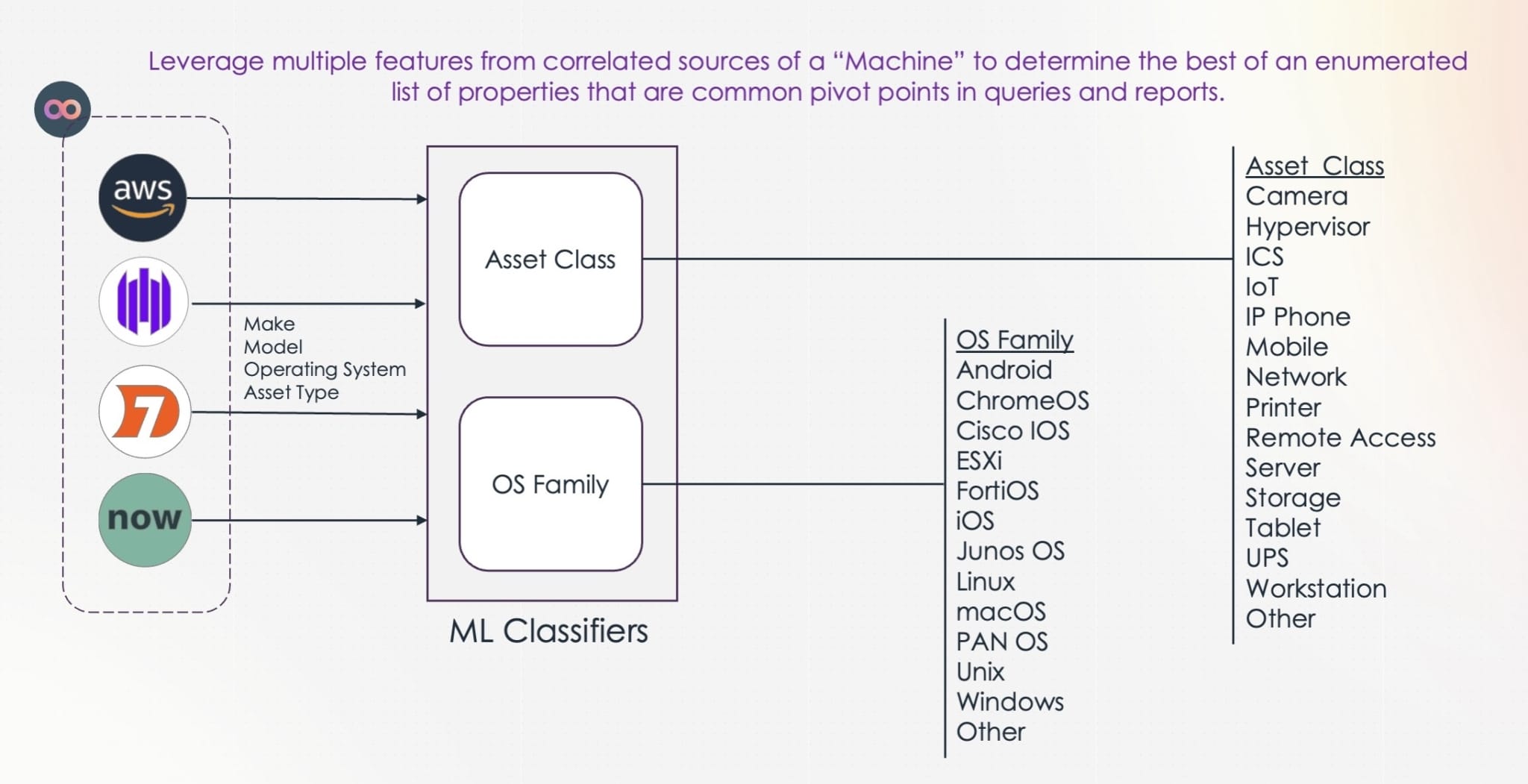
These classifiers have been extensively tested and are already delivering a high degree of accuracy on customer data. We believe that this is a great example of how Noetic’s ability to draw context and relationships from large, disparate datasets is delivering real value to our customers. We expect to deliver continuous enhancements and additions to our analytics capabilities, further enhancing our customers’ abilities to easily explore and gain insights from their consolidated cyber asset data.

High fidelity data leads to better security decision making, you can join us at this year’s last live demo on December 13th at 11:00am ET to learn more about how Noetic is helping our customers to get more accurate insights and improve their security posture.
*** This is a Security Bloggers Network syndicated blog from Noetic: Cyber Asset Attack Surface & Controls Management authored by [email protected]. Read the original post at: https://noeticcyber.com/machine-learning-in-cyber-asset-inventory/


