Penetration Testing for Sensitive Data Exposure in Enterprise Networks: Everything You Need to Know!
The amount of data enterprises store is much bigger than SMBs. A lot of this data includes sensitive information of customers and clients such as bank details, social security numbers, emails, contact numbers, etc. These data help organizations function efficiently but are always prone to cyber threats. Due to this, businesses have to follow strict privacy regulations such as the CCPA and GDPR to ensure the safety of these data. If failed, a hefty amount for non-compliance is always on the card. It is where penetration testing comes to the rescue.
For those new to data security, penetration testing is a simulated cyberattack against your computer systems to check for exploitable vulnerabilities. It’s a bit like a fire drill but for your network’s security. But before diving into the details of penetration testing, let’s discuss sensitive data exposure.
What is Sensitive Data Exposure?
Sensitive data exposure happens when an organization’s precious bytes, containing personal, financial, or business-critical information, are well indecently exposed. It’s a no-brainer that you want to avoid such situations at all costs!
Data Exposure vs. Data Breach: Understanding the Key Differences
Data exposure and data breach are often used interchangeably, but they have distinct meanings. Both situations are dangerous, but the intent and method are different. It’s important to understand this distinction to take appropriate precautions and protect your data.
Data Exposure:
- Unintentional: Sensitive data becomes accessible to unauthorized individuals due to errors or misconfigurations.
- Accidental: Examples include misconfigured cloud storage, publicly accessible servers, or lost laptops containing sensitive information.
- Passive: No active attempt to steal data.
- Internal or external: This can happen within an organization or through external exposure.
Data Breach:
- Intentional: Malicious actors actively steal data through hacking, phishing, or other attacks.
- Targeted: Attackers specifically aim to steal data for personal gain (identity theft, financial fraud, etc.).
- Active: Requires sophisticated techniques and tools.
- External: Always involves unauthorized access from outside the organization.
Data exposure is like accidentally leaving your door unlocked, whereas a data breach is like someone breaking into your house.
How Do Sensitive Data Exposures Lead to Attacks?
Sensitive data can be exposed in various ways, depending on its state: data in transit, data at rest, and data in use. Here’s a breakdown of potential exposure points for each state:
- Data in Transit
- Data in Rest
- Data in Use
1. Data in Transit
- Insecure communication channels: Sending sensitive data over unencrypted channels like HTTP or unencrypted email can allow attackers to intercept and steal the data.
- Man-in-the-middle attacks: Hackers can intercept communication between two parties and steal sensitive data in transit.
- Weak encryption protocols: Using outdated or weak encryption algorithms can make it easier for attackers to decrypt sensitive data.
- Misconfigured systems: Improperly configured systems can expose sensitive data in transit, such as leaving ports open that shouldn’t be.
- Insider threats: Malicious actors within an organization can access and steal sensitive data as it is transmitted between systems.
2. Data at Rest
- Unsecured databases and storage devices: Storing sensitive data on unencrypted devices or databases without proper access controls makes it vulnerable to unauthorized access.
- Misconfigured cloud storage: Improperly configured cloud storage buckets can expose sensitive data publicly to anyone on the internet.
- Lost or stolen devices: If a device containing sensitive data is lost or stolen, the data can be accessed by anyone who finds it.
- Physical access attacks: Attackers can gain physical access to servers or storage devices and steal sensitive data.
- Insider threats: Similar to data in transit, malicious actors within an organization can access and steal sensitive data at rest.
3. Data in Use
- Weak access controls: Granting access to sensitive data to unauthorized users or granting excessive permissions can increase the risk of exposure.
- Malware and phishing attacks: Malware can be used to steal sensitive data from infected devices, and phishing attacks can trick users into revealing sensitive information.
- Insecure coding practices: Applications with vulnerabilities, such as SQL injection or cross-site scripting, can allow attackers to steal sensitive data.
- Session hijacking: Attackers can hijack a user’s session and gain access to the sensitive data they are working with.
- Insider threats: Once again, malicious actors within an organization can access and steal sensitive data while it is being used.
How to Protect Sensitive Data from Getting Exposed?
It’s crucial to implement security measures to protect sensitive data in all three states:
- Data in transit: Use strong encryption protocols and secure communication channels like HTTPS.
- Data at rest: Encrypt sensitive data at rest, implement strong access controls, and regularly back up data to secure locations.
- Data in use: Implement strong access controls, train employees on cybersecurity awareness, and use security software to detect and prevent malware and phishing attacks.
Common Data Infiltration Methods:
- Phishing: Tricking users into clicking malicious links or attachments.
- Malware: Installing harmful software on devices to steal data.
- Weak Passwords: Hackers easily guess or crack simple passwords.
- Data Leaks: Insider threats or accidental exposure.
- Social Engineering: Manipulation tactics to gain access or information.
- Unpatched Systems: Outdated software with known vulnerabilities.
- Physical Access: Stolen devices or bypassing physical security measures.
Now you have the idea of sensitive data exposure, it’s time to understand more about the role of penetration testing in enterprise security.
Why Penetration Testing is Crucial for Enterprises?
Pentesting is less of a choice and more of a necessity to protect your company’s valuable data from the ever-present threat of cyberattacks.
Here are several reasons why penetration testing is crucial for enterprises:
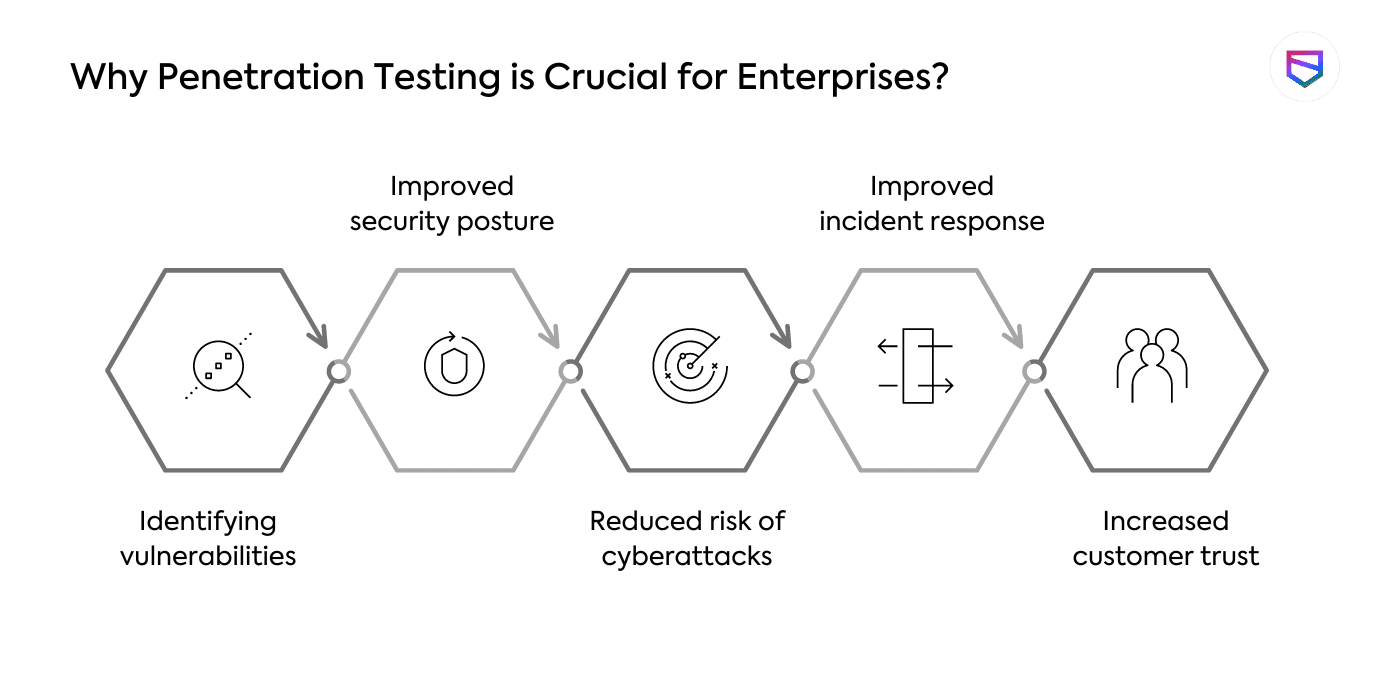
-
Identifying vulnerabilities:
- Pentesting helps uncover security weaknesses that hackers could exploit to gain unauthorized access to sensitive data, disrupt critical operations, or cause financial harm.
- It goes beyond basic vulnerability scans by simulating real-world attack scenarios and attempting to bypass security controls.
- This proactive approach allows organizations to address vulnerabilities before a malicious actor exploits them.
-
Improved security posture:
- Pentesting helps organizations gain valuable insights into their overall security posture and identify areas that need improvement.
- This information can be used to prioritize security investments and implement effective security controls.
- Penetration testing can also help organizations comply with industry regulations and standards that require regular security assessments.
-
Reduced risk of cyberattacks:
- Identifying and addressing vulnerabilities before they can be exploited significantly reduces the risk of successful cyberattacks.
- This can help organizations protect their sensitive data, maintain operational continuity, and avoid the financial and reputational damage associated with cyberattacks.
-
Improved incident response:
- Pen testing can help organizations identify gaps in their incident response plans and procedures.
- By simulating real-world attacks, organizations can test their ability to detect, respond to, and recover from security incidents.
- This helps them improve their incident response capabilities and minimize the impact of cyberattacks.
-
Increased customer trust:
- Demonstrating a commitment to security through regular pen testing can help organizations build trust with their customers and partners.
- This is particularly important for organizations that handle sensitive data or operate in highly regulated industries.
Additional benefits of penetration testing include:
- Improved security awareness among employees
- Enhanced security architecture and design
- Identification of potential compliance issues
- Cost savings by avoiding costly data breaches and downtime
Pre-Penetration Testing Considerations
Like any complex endeavor, effective pen testing requires careful planning and preparation. Before launching into the simulated attack, let’s address several key considerations to ensure success and productivity.
Setting Goals and Objectives:
- What do you want to achieve with the pen test? Are you looking to identify specific vulnerabilities, assess the overall security posture of your systems, or comply with regulatory requirements?
- What are your key success metrics? How will you measure the effectiveness of the pen test?
- What resources are available to you? This includes budget, personnel, and access to systems and data.
Defining the Scope:
- Which systems and applications will be included in the pen test? Prioritize high-value assets and critical infrastructure.
- What types of attacks will be authorized? This could include black-box, white-box, or gray-box testing, depending on your objectives.
- What are the limitations of the scope? Clearly define what is and is not included in the pen test to avoid confusion and misinterpretations.
Legal and Regulatory Considerations:
- Do you have the necessary permissions and approvals to conduct a pen test? This may involve internal stakeholders, regulatory bodies, or third-party vendors.
- Are there any legal or compliance requirements that you need to comply with? This could include data privacy regulations or industry standards.
- What are the reporting and notification requirements? Ensure you understand how to communicate the results of the pen test to relevant stakeholders.
Additional Pre-Engagement Considerations:
- Choosing the right pentesting methodology: Black-box, white-box, or gray-box testing each has its advantages and disadvantages. Choose the method that best aligns with your goals and resources.
- Selecting the right pen testing team: Consider factors such as experience, expertise, and certifications when choosing a pen tester.
- Establishing communication channels: Clearly define how you will communicate with the pen testing team throughout the engagement.
- Developing a risk assessment: This will help you prioritize vulnerabilities and allocate resources effectively.
- Creating a rollback plan: In case the pen test identifies critical vulnerabilities, have a plan in place to quickly remediate them.
Here are some additional resources that you may find helpful:
- The Penetration Testing Execution Standard (PTES): https://pentest-standard.readthedocs.io/
- The National Institute of Standards and Technology (NIST) Special Publication 800-53: https://csrc.nist.gov/pubs/sp/800/53/r5/upd1/final
- The Open Web Application Security Project (OWASP) Top 10: https://owasp.org/www-project-top-ten/
The Penetration Testing Process
Penetration testing is a methodical process with several key stages, each playing a vital role in uncovering and mitigating potential threats. Here’s the breakdown.
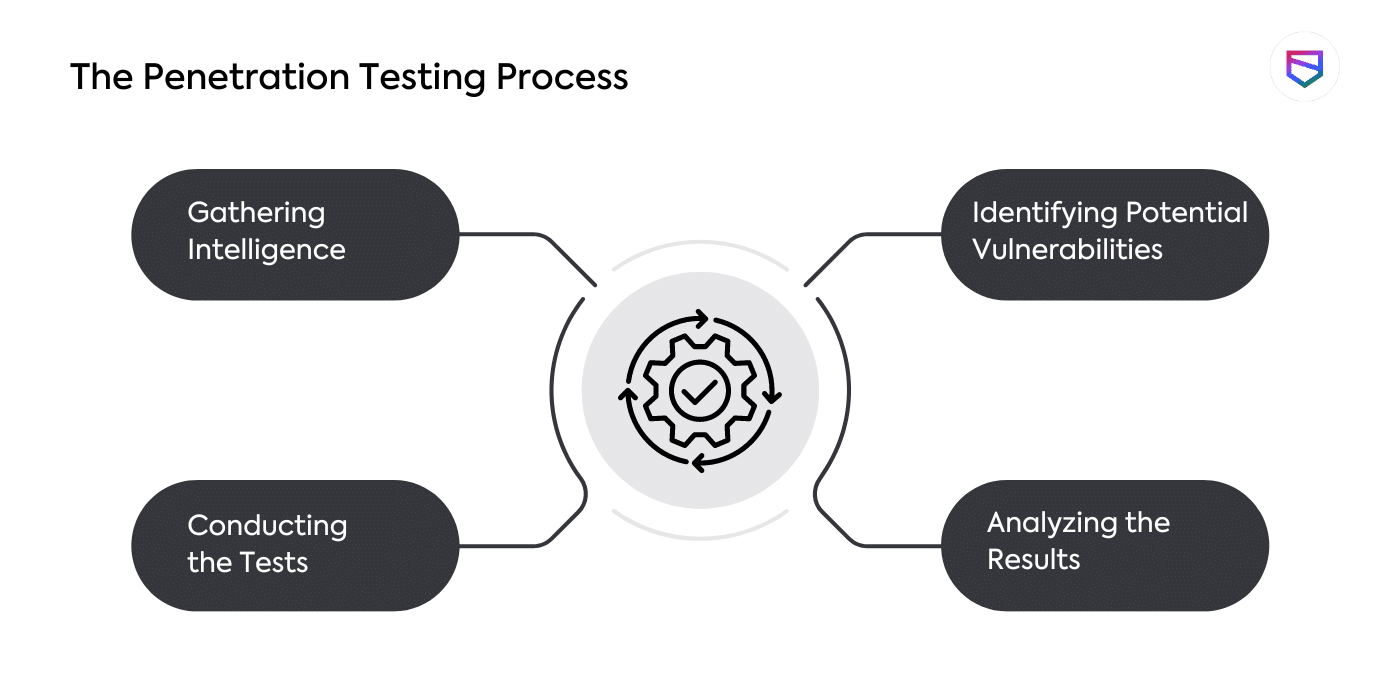
1. Gathering Intelligence
This initial stage involves acquiring knowledge about the target systems and networks. It includes:
- Information gathering: Research the organization’s website, social media presence, and other public sources to identify potential attack vectors.
- Open-source intelligence (OSINT): Utilizing publicly available information to gain valuable insights into the organization’s infrastructure and security posture.
- Social engineering: Employing techniques to gather information from employees or individuals with access to sensitive data.
2. Identifying Potential Vulnerabilities
Based on the gathered intelligence, the pen tester identifies potential vulnerabilities in the target systems and networks. This includes:
- Scanning and enumeration: Using automated tools to identify open ports, services, and user accounts.
- Vulnerability assessments: Analyzing the discovered vulnerabilities to determine their severity and potential impact.
- Manual testing: Employing manual techniques to identify vulnerabilities that may be missed by automated tools.
3. Conducting the Tests
Once the potential vulnerabilities have been identified, the pen tester begins conducting simulated attacks. This involves:
(a)Techniques and Tools
The pen tester utilizes a variety of techniques and tools to exploit the identified vulnerabilities. These may include:
- Exploits: Utilizing known exploits to gain unauthorized access to systems and networks.
- Social engineering: Employing targeted phishing attacks or other techniques to manipulate users into divulging sensitive information.
- Password cracking: Attempting to crack user passwords to gain access to accounts.
(b)Simulating Attacks
The pen tester simulates real-world attacks to understand the potential impact and effectiveness of an actual attack. This may include:
- Lateral movement: Moving within the network to gain access to additional systems and data.
- Data exfiltration: Stealing sensitive information from the organization’s systems.
- Privilege escalation: Gaining higher levels of access within the network.
4. Analyzing the Results
After conducting the simulated attacks, the pen tester analyzes the results to identify the critical findings and risks. It consists of:
(a) Critical Findings and Risks
The pen tester identifies the most critical vulnerabilities exploited during the testing process. This includes vulnerabilities that could lead to a significant security breach or data loss.
(b) Formulating Remediation Strategies
Based on the identified vulnerabilities and risks, the pen tester develops a comprehensive remediation plan. This plan includes:
- Prioritizing the vulnerabilities: Focusing on the most critical vulnerabilities first.
- Developing clear steps for remediation: Providing detailed instructions for addressing each vulnerability.
- Estimating the resources and costs: Identifying the personnel and budget required for remediation.
- Timeline for implementation: Establishing deadlines for completing the remediation tasks.
Post-Penetration Testing Actions
-
Reporting and Documentation
a) Transparency and Detailing the Findings:
- Create a clear and concise report outlining identified vulnerabilities, severity levels, and potential impacts.
- Include detailed steps taken during the test and evidence of findings for verification.
- Share the report with key stakeholders involved in security and decision-making processes.
b) Constructive Feedback Loop:
- Facilitate discussions and workshops to discuss the report findings and address concerns.
- Encourage open communication and feedback from all parties involved.
- Establish a process for incorporating the findings into future security strategies.
-
Remediation and Patches
a) Mitigation Steps and Solutions:
- Develop a comprehensive plan to address the identified vulnerabilities based on their risk level and feasibility.
- Prioritize critical vulnerabilities and implement immediate mitigation measures.
- Assign clear roles and responsibilities for implementing the remediation plan.
b) Monitoring and Continuous Assessment:
- Implement automated vulnerability scanning and monitoring tools to track progress and identify new threats.
- Conduct periodic penetration tests to assess the effectiveness of implemented security measures.
- Continuously update and improve security policies and procedures based on evolving threats and vulnerabilities.
Best Practices for Penetration Testing
- Regular Penetration Testing Schedule
Don’t wait for a security incident to occur before conducting a pen test. Establish a regular schedule for pen testing, ideally at least once a year or more frequently if your organization deals with sensitive data or operates in a high-risk environment. This allows you to identify and address vulnerabilities before attackers can exploit them.
- Employing Ethical Hackers
For maximum effectiveness, consider engaging the services of professional ethical hackers. These individuals possess in-depth knowledge of hacking techniques and tools and can simulate sophisticated attacks that mirror the real world. They can test your organization’s security defenses across various attack vectors, providing valuable insights into your vulnerabilities.
- Continuous Education and Training
Technology and cyber threats evolve rapidly. To maintain a strong security posture, it’s crucial to invest in continuous education and training for your IT staff and security personnel. This ensures they are equipped with the latest knowledge and skills to identify, assess, and remediate vulnerabilities effectively.
Common Pitfalls and How to Avoid Them
Despite the benefits of penetration testing, several common pitfalls can hinder its effectiveness. It’s important to be aware of these pitfalls and take steps to avoid them.
- Underestimating Attack Vectors
A common mistake organizations make is focusing primarily on external attacks while neglecting internal threats. Attackers can leverage various internal vulnerabilities, such as weak passwords, unpatched systems, and social engineering techniques, to gain access to sensitive data.
How to Avoid:
- Conduct regular vulnerability assessments and penetration tests across all systems and networks, including internal infrastructure.
- Implement strong security controls, such as access controls, data encryption, and endpoint security solutions.
- Address insider threats by implementing a least privilege access model, monitoring user activity, and conducting regular security awareness training.
- Overlooking Insider Threats
While external attacks are often the focus of security efforts, insider threats can pose a significant risk. Disgruntled employees, contractors, or even business partners can misuse their access to steal data, disrupt operations, or sabotage systems.
How to Avoid:
- Implement a least privilege access model, granting users only the minimum access required for their roles.
- Conduct regular background checks and security awareness training for all employees and contractors.
- Monitor user activity for suspicious behavior and implement a system for reporting security incidents.
- Failing to Update Security Measures
Security threats are constantly evolving, and so should your security measures. Organizations that fail to update their security tools, software, and policies are more vulnerable to attacks.
How to Avoid:
- Patch software vulnerabilities promptly.
- Update security tools and technologies regularly.
- Review and update security policies and procedures to reflect the latest threats and best practices.
Tools of the Trade: Unveiling Sensitive Data with Penetration Testing
Let’s explore some widely used tools in the penetration testing:
1. Nmap
This open-source tool is a staple for network mapping and service discovery. Nmap allows pentesters to identify open ports, running services, and operating systems on devices within a network. This information is invaluable for determining potential attack vectors and prioritizing targets.
Strengths: Extensive scanning capabilities, flexible scripting options, open-source with a large community.
Use cases: Identifying open ports for further exploration, determining network topology, discovering vulnerable services.
2. Wireshark
This network protocol analyzer captures and analyzes network traffic in real-time. Wireshark allows pentesters to inspect individual packets, identify sensitive data transmission, and analyze network protocols for vulnerabilities.
Strengths: Deep packet inspection, comprehensive protocol support, extensive filtering and analysis capabilities.
Use cases: Detecting unencrypted data transmission, identifying sensitive data leaks, analyzing network traffic for anomalies.
3. Metasploit
This framework provides a vast library of exploit code for various vulnerabilities across different platforms. Metasploit allows pentesters to automate exploit execution and gain access to target systems.
Strengths: Extensive exploit library, automation capabilities, customizable payloads, large community for contributions.
Use cases: Exploiting known vulnerabilities, gaining initial access to target systems, automating repetitive tasks.
4. SQLmap
This automated tool specializes in detecting and exploiting SQL injection vulnerabilities in web applications. SQLmap can bypass authentication, extract sensitive data, and even take over the database server.
Strengths: High accuracy in detecting SQL injection, automated exploitation capabilities, diverse extraction and manipulation functionalities.
Use cases: Identifying vulnerable web applications, extracting sensitive data from databases, demonstrating the impact of SQL injection.
5. Burp Suite
This integrated platform offers a comprehensive suite of tools for web application penetration testing. Burp Suite includes tools for intercepting and modifying web requests, analyzing application vulnerabilities, and testing authentication mechanisms.
Strengths: User-friendly interface, extensive feature set, modular architecture for customization, large community for extensions.
Use cases: Identifying web application vulnerabilities, testing authentication bypass techniques, intercepting and modifying web traffic.
WeSecureApp: Guarding your Enterprise Against Data Exposure
Cybersecurity is no longer a “maybe”, it’s a “must-have”. A single data breach can have devastating consequences, damaging your reputation, costing you millions, and eroding customer trust. That’s why at WeSecureApp, we’re passionate about helping organizations like yours mitigate risk and ensure data security.
Our pentesting services go beyond identifying vulnerabilities. We go deep, simulating real-world attack scenarios to expose weaknesses before malicious actors exploit them. We help you understand how attackers think, enabling you to proactively address vulnerabilities and patch security holes before they’re weaponized.
But penetration testing is just one piece of the puzzle. True security requires a multi-layered approach. We offer a suite of solutions tailored to your specific needs.
By partnering with WeSecureApp, you gain access to a team of experienced cybersecurity professionals. We don’t just provide solutions, we build long-term partnerships, ensuring your security needs are met today, tomorrow, and beyond.
Don’t risk your sensitive data! Contact WeSecureApp today to schedule your free penetration testing consultation.
The post Penetration Testing for Sensitive Data Exposure in Enterprise Networks: Everything You Need to Know! appeared first on WeSecureApp :: Simplifying Enterprise Security.
*** This is a Security Bloggers Network syndicated blog from WeSecureApp :: Simplifying Enterprise Security authored by Shubham Jha. Read the original post at: https://wesecureapp.com/blog/penetration-testing-for-sensitive-data-exposure-in-enterprise-networks-everything-you-need-to-know/


