Understanding and Mitigating the Fedora Rawhide Vulnerability (CVE-2024-3094)
CVE-2024-3094 is a reported supply chain compromise of the xz libraries. The resulting interference with sshd authentication could enable an attacker to gain unauthorized access to the system.
Overview
Malicious code was identified within the xz upstream tarballs, beginning with version 5.6.0. This malicious code is introduced through a sophisticated obfuscation technique during the liblzma build process. A prebuilt object file is extracted and cleverly hidden within a test file in the source code. This object file then alters specific functions within the liblzma code. Consequently, any software that relies on this compromised version of liblzma may unknowingly interact with a modified library. This manipulation allows for the interception and alteration of data handled by the library.
A great breakdown can be found on linuxiac.com.
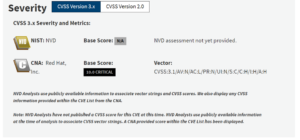
CVE-2024-3094 was likely detected before it could significantly impact downstream production, preventing widespread issues. This early detection is reassuring and highlights the importance of vigilance, yet it shouldn’t lead to a false sense of security. You should take the following steps:
- Detect your exposure
First and foremost, identify your level of exposure by checking if you’re using XZ tools versions 5.6.0 and 5.6.1. Those running Fedora Linux 40 or any Fedora Rawhide instance are at direct risk of receiving the backdoored package. Notably, RedHat Enterprise instances should be spared from this vulnerability. - Assess SSH Access
Given the nature of the threat, evaluating your SSH access to potential threat vectors is essential. Limiting your SSH exposure immediately is critical to mitigate further risks if you find yourself exposed. - Take Action
CISA recommends that developers and users downgrade XZ Utils to an uncompromised version, such as XZ Utils 5.4.6 Stable, to look for malicious activity and report any positive findings to CISA. Additional advice can be found here.
How do I look for the package with OX
Test your applications within the OX Active ASPM Platform. (Note: you can sign up for a free trial if you don’t have OX. The connection is agentless,is based on APIs, and takes less than a minute to deploy.)
- Log in
- The platform will automatically scan your connected environment from code to cloud.
- It will detect direct uses of XZ libraries and will alert the vulnerable ones.
To discover the usage of XZ libraries:
- Search for CVE-2024-3094 or in Issues
- It will find all direct and indirect xz utils libraries and show the version used. Note: The stable versions of Linux distros were not affected. It’s mostly beta/dev branches of those OSs
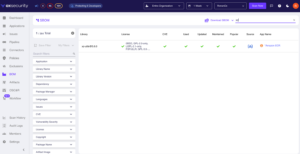
The example shows that it is not Fedora and is free from malicious code. Running the scan saves time as you do not have to review multiple applications.
On-going tracking and community collaboration
Thank you to Andres Freund for his pivotal role in identifying and reporting CVE-2024-3094, Lasse Collin, the maintainer of xz-utils, for promptly providing updates and working alongside the community to mitigate the security risks involved, and to the security teams whose swift actions have been crucial in coordinating a response. Your contributions, underscored by collaborative efforts, are immensely valued and show how community is essential in averting larger incidents.
OX Security will continue to monitor this situation and provide updates as events unfold. Follow us on Linkedin and check the OX Security Blog for any developments.
Additional resources – Courtesy of Latio Tech
Here are the main links from different providers:
- Red Hat (stable, not vulnerable)
- Debian (stable, not vulnerable)
- Suse (stable, not vulnerable)
- Kali (Impacted but exploit not confirmed)
- Arch (Impacted but exploit not confirmed)
- Homebrew (Impacted but probably not exploitable)
- FreeBSD (not impacted)
- Amazon Linux (not impacted)
The post Understanding and Mitigating the Fedora Rawhide Vulnerability (CVE-2024-3094) appeared first on OX Security.
*** This is a Security Bloggers Network syndicated blog from OX Security authored by Lior Arzi. Read the original post at: https://www.ox.security/understanding-and-mitigating-the-fedora-rawhide-vulnerability-cve-2024-3094/


